Description of the service of threat modelling using MITRE ATT&CK framework
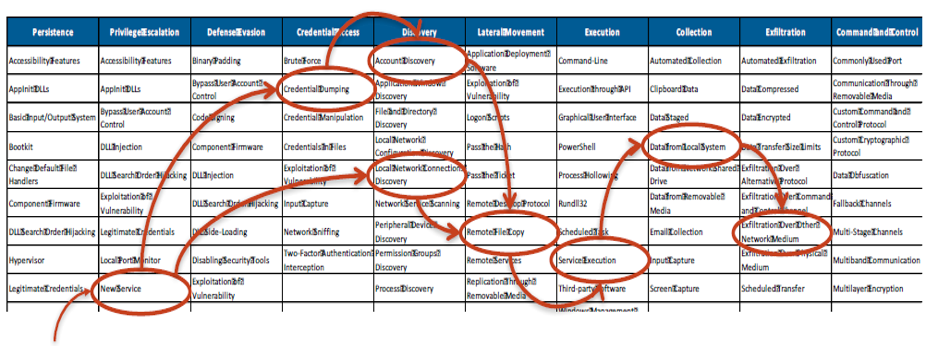
MITRE ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) is a knowledge base of attack methods used by cybercriminals. ATT&CK contains 12 tactics (Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, Impact) that are the steps an attacker can use to accomplish an attack objective. There is a number of techniques associated with each tactic. Techniques are the methods by which attackers accomplish the objectives of each tactic. Tactics and associated techniques form a detailed matrix enabling the assessment of the way that events might occur (what techniques might be used) in a given environment. The modelling will also consider the identification of links and flows between techniques.
Threat modelling with the use of MITRE ATT&CK is a service that identifies attack techniques that attackers can use in the environment under examination.
The ComCERT SA team, along with representatives of the Ordering Party, analyse selected systems to answer the following questions:
- What techniques can be used against the Ordering Party (taking into account the technological solutions used)?
- What safeguards against identified techniques are in place?
- How can we detect the use of identified attack techniques (what logs are collected in the tested environment and are they sufficient to detect the technique)?
As a result of the modelling, the Ordering Party receives information about:
- Attack techniques applicable to the Ordering Party’s environment including ITSec systems.
- Prevention methods in relation to identified techniques.
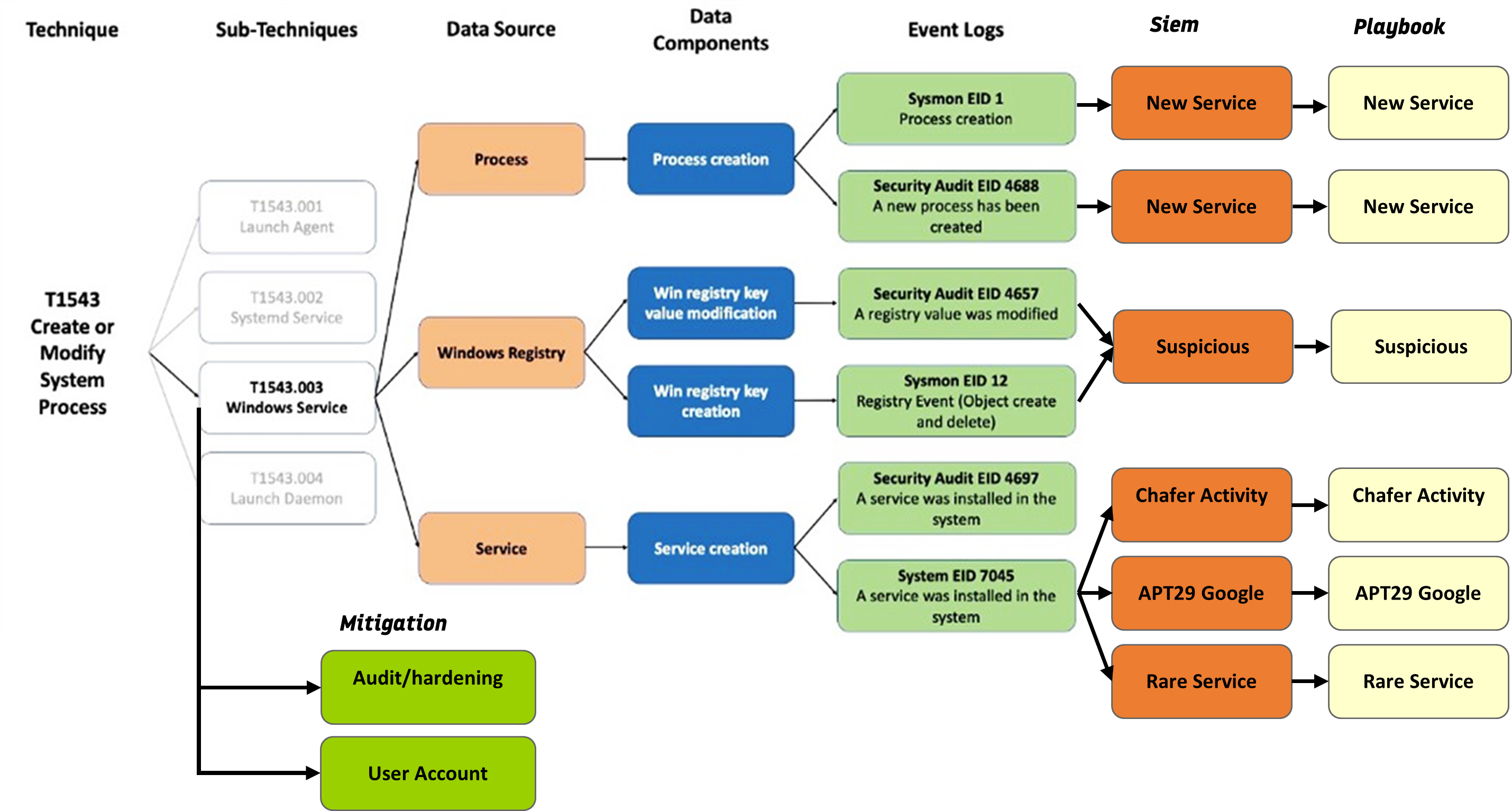
- Events logged in the environment and their sources to detect the use of a particular attack technique.
- Identification of possible gaps in terms of detection of attack techniques logged in the environment.
- Identification which log sources can be run (including evaluating the option to enable logging of additional events) and which require additional actions.
- Identification of opportunities to use alerts from ITSec systems to detect and prevent the use of identified attack techniques.
Example of building potential attack scenarios
Example of using information on attack techniques to identify necessary logs and build correlation rules for detection